
― Med Amine Khelifi
Member-only story
Hacking in 5 minutes with Remote Procedure Call and Active Directory enumeration
Before we start going deeper,let me introduce you what is RPC(Remote Procedure call)?, based on Microsoft documentation:

Moment I encounter window server machine that available RPC service, I try to fully utilize the enumeration of service by using rpcclient.
what is rpcclient? it is tool for executing client side MS-RPC functions.
rpcclient [-A authfile] [-c <command string>] [-d debuglevel] [-l logdir] [-N] [-s <smb config file>] [-U username[%password]] [-W workgroup] [-I destinationIP] {server}
rpcclient support many command options to execute MS-RPC function,these command can be placed under several categories,LSARPC,LSARPC-DS,REG,SRVSVC,SAMR,SPOOLSS,NETLOGON,FSRVP
LSARPC is really a set of calls, transmitted with RPC, to a system called the “Local Security Authority”. This used in the Microsoft/Windows world to perform management tasks on domain security policies from a remote machine. The protocol is described in MS-LSAD. The transport medium is RPC, a part of the “Server Message Block” protocol (MS-SMB, MS-SMB2).(https://security.stackexchange.com/questions/80167/how-does-lsarpc-protocol-work)
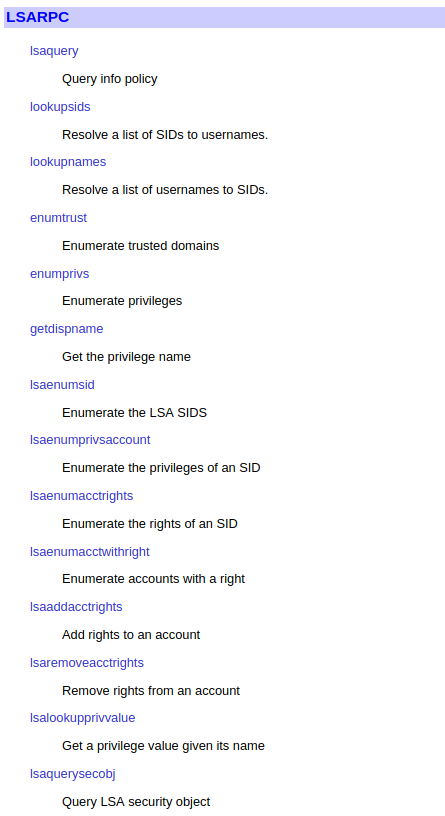
For example, If you allowed to login using “Null” , you can query for domain info by command “querydominfo”.


LSARPC-DS is use to get primary domain information.

